2019 Data Breach Predictions and Findings
Prediction: Large-scale social media attacks leading to massive personal data losses.
Findings: We saw a number of social media sites leaking data. A lot of that was personal in nature, things like usernames and passwords. And Facebook didn’t let us down with this prediction. In 2019, 267 million Facebook users had their identifying information–including phone numbers–exposed. In a separate breach earlier in the year, 540 million Facebook accounts were exposed, and the month prior to that one, 600 million Facebook accounts were exposed.
It’s important to note that the number of victims in each reported breach is not cumulative, these are each individual incidences, bringing the total between these three breaches to upwards of 1.4 billion victims.
Read our Data Breach Predictions blog from 2019.
Prediction: Biometric data will be compromised
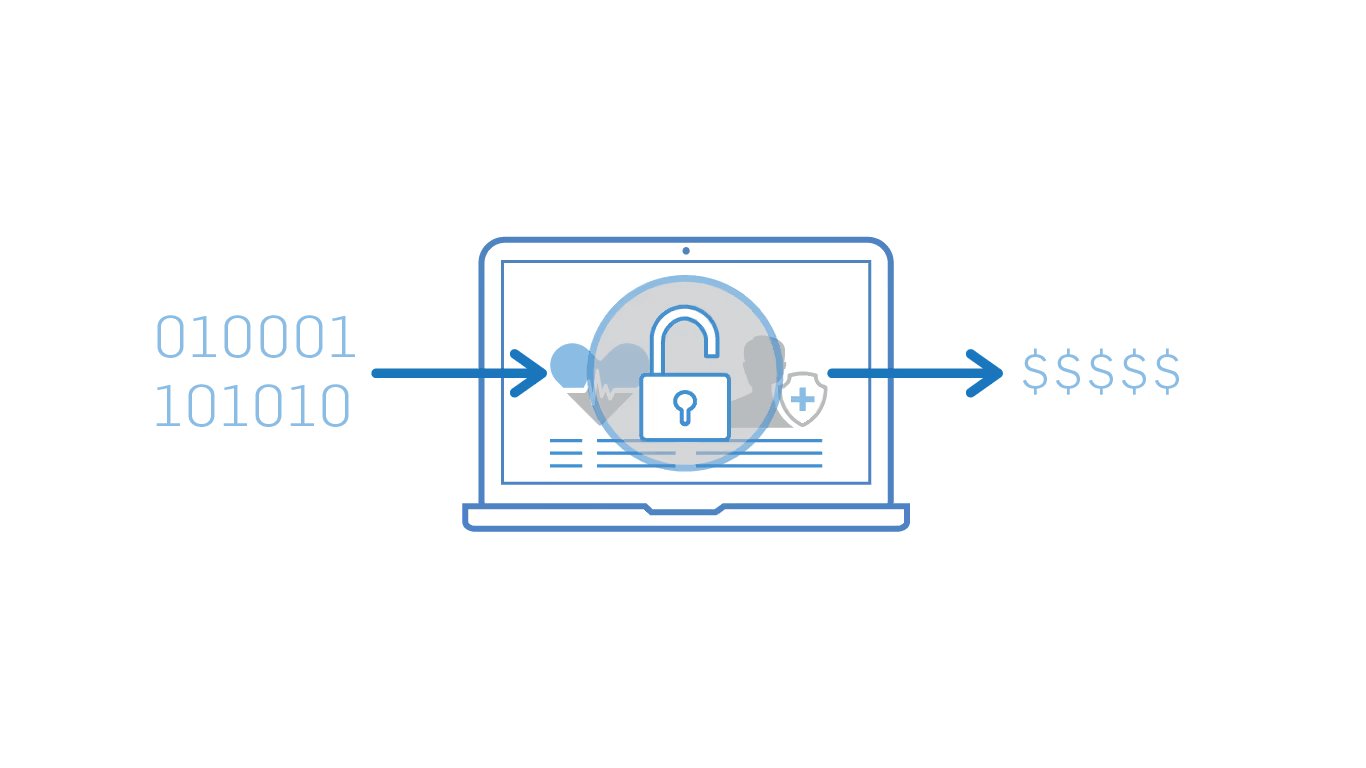
Findings: Fingerprints, eye scans, and facial recognition are some examples of the biometric data that organizations may collect from customers and employees. One organization lost a number of facial photos used for authentication, as well as fingerprints from 5,700 organizations in 83 different countries. Overall, they lost the data of more than 1 million people.
If you lose a username or password, you can simply go and change that. However, if you lose your employee’s fingerprints, the repercussions will likely be more serious.
Prediction: Cloud provider will be seriously breached
Findings: All of the the emphasis on Amazon’s Simple Storage Service (S3) buckets drew attention from attackers as well. If you remember, some S3 buckets’ access settings were defaulted to “public.” Many are still dealing with the blowback from Amazon’s misconfiguration today. We still see large breaches that started with public access on the S3 buckets.
Capital One Bank also suffered a massive cloud-related breach that included account data from over 100 million customers. A former employee of Amazon Web Services was aware of the methodology needed to steal account data without triggering safety protocols within the organization. This could be considered an insider attack, although the employee was no longer with Amazon. Capital One made the mandated notifications and then remediated the issue.
There are merchants and individuals that may feel storing data in the cloud removes the need to worry about it, but you still need to be on top of security. There will always be flaws and vulnerabilities with any service. It’s important to know which party is responsible for which data security activities.
Prediction: Foreign nation-states will increase recruitment of corporate insiders to steal industry secrets.
Findings: While our government contacts can neither confirm nor deny the increase of such attacks, they did imply that state-sponsored hacking activities are still going on, and they typically only become public when they need to make a high-profile arrest.
Prediction: Passwords may not be the security you’re looking for.
Findings: Passwords continue to have issues. With the release of massive databases containing billions of passwords, these issues are complicated even further. In our forensic research here at SecurityMetrics, our ability to test and crack passwords in the last year has skyrocketed. We maintain our own databases with billions of passwords. Global password-cracking technology is accelerating and spreading at a rate that diminishes their security significantly. Some technologies are to the point where they can crack any password up to a full 20 characters in a matter of a day or two.
Computing that currently takes days will eventually turn into hours, then seconds, milliseconds, and nanoseconds. When you combine that fact with a huge public cache of passwords stored in a text file, cracking passwords becomes easy work.
One of the issues that has sprung out of this is a scam where hackers send emails saying “We have your password, and we caught you doing something bad. So send us this amount of money to avoid us releasing your compromising data.” The hackers then show you they have your legitimate password (obtained from a password cache). If you do see this scam come through your email, make sure to change your password immediately.
2020 Data Breach Predictions
More attacks targeted against cloud-based products, services, and platforms
Many organizations are moving their products and services to cloud-based solutions. We predict that we will see attacks specifically adapted and targeted to cloud-based services, including message platforms like live chat applications and storage solutions, and especially to JavaScript code that is delivered from a cloud-based content delivery network. A little bit of effort can yield a big payoff with these kinds of attacks.
Spike in registration of look-alike domain names for evil purposes
We will see many bad actors using look-alike domain names to target customers of legitimate business. To avoid these attacks, merchants should register domain names that are similar to their own.
Artificial Intelligence vs. Artificial Intelligence
We predict an increase in attackers embedding malware in AI while it’s still in its learning phase so it will recognize the malware as an allowable element in its environment. This will be done in the hopes that the AI program will continue to allow malware into the environment in the future.
A word on E-commerce skimming or "Magecart" attacks
As predicted, the move to EMV, or “chip,” security in payment cards has shifted criminals’ efforts away from card-present fraud–such as physical card skimming–and put the focus on e-commerce JavaScript injection on shopping cart pages. Attackers tend to take a “shotgun” approach, compromising as many websites as possible at a time, hoping that some might turn out to be lucrative.
E-commerce skimming or "Magecart" attacks are “insidious and nasty, yet so simple,” according to SecurityMetrics CEO Brad Caldwell. All cybercriminals have to do is load malicious code into e-commerce shopping cart pages, disguise them well enough to be missed, and wait for the submissions to come in. In some cases, malicious code is disguised as a google tag or as a domain that sounds related to the website or payment processor.
Symantec reported that on average, 4,800 unique websites are compromised with malicious code each month. This ongoing effort by cybercriminals targets providers of all sizes. Recent research by RiskIQ reported that such attacks by the “Magecart” group are actually much more widespread than initially believed.
What is Magecart?
Known to be active since 2015, "Magecart" refers to at least seven different hacking groups and has become a household name in recent years as these groups were responsible for the well-known cyberattacks on large companies including British Airways, Ticketmaster, and Newegg.
Magecart attack methods involve browser-based injection of malicious Javascript code, often well-disguised as a Google tag or other common website analytics code snippet. This malicious code "skims" form entry fields for payment card data, names, addresses, and even personal information or protected health information (PHI)–depending on what type of website is attacked.
Magecart attackers are best known for hacking into Magento shopping cart pages, but they are not limited to just Magento, or even to payment card data. These e-commerce skimming attacks have been discovered on many typs of pages and sites including healthcare and banking.
Skimming through malicious adware, or "malware"
One way hackers introduce Javascript skimming onto e-commerce pages is through scrolling or rotating ads. When a scrolling ad network introduces malware, we typically see intermittent card data loss. Within a period of a few minutes, a customer's credit card and personal information can be siphoned.
We have seen attackers hack into ad networks and we have also seen more sophisticated hackers invent entire products to trick ad companies into accepting their malicious ads. This is a brilliant strategy on the part of the hacker–they build one tool (their "ad" laced with malicious code) and a third party (the ad network) distributes the tool to hundreds of websites.
How to detect e-commerce skimming
E-commerce skimming has no telltale signs. There is no way for a consumer to detect a skimming attack on a shopping cart page while it’s happening, and it’s very difficult for the merchant or payment processor to pick up on. Any provider that is “downstream” from the affected website can also be affected without the provider’s knowledge.
When the code on a webpage is compromised, you don’t have typical hints–such as a spoofed URL or non-secure WiFi connection–to alert you that something is wrong. It can take many hours of manual research and work to discover and remove malicious code.
Some companies claim that products like antivirus or scanning software can detect instances of malicious code insertion, but that is not always the case.
Why traditional security measures don’t stop Magecart or e-commerce skimming
A high-end antivirus software may provide some protection for the consumer, but the most commonly used tool to detect unwanted changes to your environment is file integrity monitoring (FIM). When FIM is deployed it will alert you when it observes changes to the files and/or folders you have set it to monitor.
Traditional FIM tools will monitor executable files, folders, system configuration files, content files, zipped files, etc. FIM is effective at detecting changes to otherwise unchanging environments. But FIM can’t help you detect changes that are made to dynamic environments, such as shopping carts, databases, and the like. Since these environments are almost constantly changing, FIM has no baseline, and therefore cannot function as an intrusion detection tool.
How to stop "Magecart" hackers
SecurityMetrics’ Webpage Integrity Monitoring (WIM) product is built on a patented technology, able to find and mitigate malicious injected code on webpages. SecurityMetrics is currently conducting a pilot program with a select few corporations.







.svg)