What the Louvre Heist Teaches Us About Cybersecurity in 2025
Here are the key takeaways from the breach and the essential cybersecurity best practices your business needs to implement in 2025 to combat threat actors.
Here are the key takeaways from the breach and the essential cybersecurity best practices your business needs to implement in 2025 to combat threat actors.

The 2025 jewel heist at the Musée du Louvre will be remembered not only as one of the most infamous robberies but also as one of the most significant cybersecurity and physical security failures.
The theft of priceless imperial jewels, stolen in a mere seven minutes, is a great lesson on how vulnerabilities mirror common failures in modern security environments.
The Louvre heist isn't just a mindblowing story about physical security; it’s a lesson in misguided priorities, catastrophic password hygiene, and the painful cost of delayed security upgrades.
Here are the key takeaways from the breach and the essential cybersecurity best practices your business needs to implement in 2025 to combat threat actors.
Read More: Auditor Tips on Password Best-Practices (Blog)
A report released by the French Court of Accounts following the October 19 heist delivered a "deafening alarm signal" about the museum's security posture.
The report revealed that leadership had prioritized "visible and attractive" projects—like art purchases and revamping the museum layout—over maintaining critical security infrastructure, which left known vulnerabilities unaddressed.
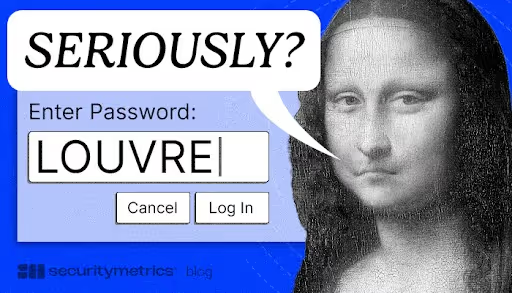
The most damning revelation for digital security professionals was the exposure of the museum's poor password hygiene.
A resurfaced 2014 warning alleged that the password for the server managing the museum’s sprawling CCTV network was simply "LOUVRE," and another system’s access (Thales) was reportedly "THALES."
This is the digital equivalent of leaving the vault keys taped to the front door.
What Businesses Must Do:
Within four minutes of arriving, the thieves had scaled the building and were breaking through a window. The alarms were only triggered after the window was broken, and the thieves were gone only four minutes later. Culture Minister Rachida Dati initially insisted the internal systems had "worked," but later conceded that “security gaps did exist.”
Louvre Director Laurence des Cars acknowledged before the French Senate, “Despite our efforts, despite our hard work on a daily basis, we failed.”
What Businesses Must Do:
Interested in strengthening your SOC team? Check out SecurityMetrics Pulse.
The Court of Accounts report revealed significant gaps in physical monitoring: only 432 CCTV cameras monitored 465 museum galleries in 2024, leaving a staggering 61% of the galleries without any coverage. Des Cars admitted that surveillance of the museum's outside walls was “highly insufficient.”
What Businesses Must Do:
The museum’s leadership was criticized for focusing on glitzy purchases, spending over €105 million on artwork while crucial security upgrades recommended in a 2015 audit won't be completed until 2032.
What Businesses Must Do:
Read More: 10 Tips for Keeping Security In the Budget (Blog)
Read More: How to Get Executive Buy-In (Blog)
The 2025 Louvre heist is a clear message that security must be a leadership priority. The museum's management was slammed for prioritizing "visible" spending over unseen but vital maintenance.
As Justice Minister Gérald Darmanin admitted following the theft, “What is certain is that we have failed, since people were able to park a furniture hoist in the middle of Paris, get people up it in several minutes to grab priceless jewels.”
For every business, the lesson is clear: your digital "jewels" are only as safe as your weakest password, your slowest response time, and your disregarded security upgrades.
Don't wait for a digital heist to force a change in your budget and your policies. The time to secure your sensitive data is now.
What will you do if you’re breached? Speak with a SecurityMetrics expert today on how to strengthen your business’s security now.