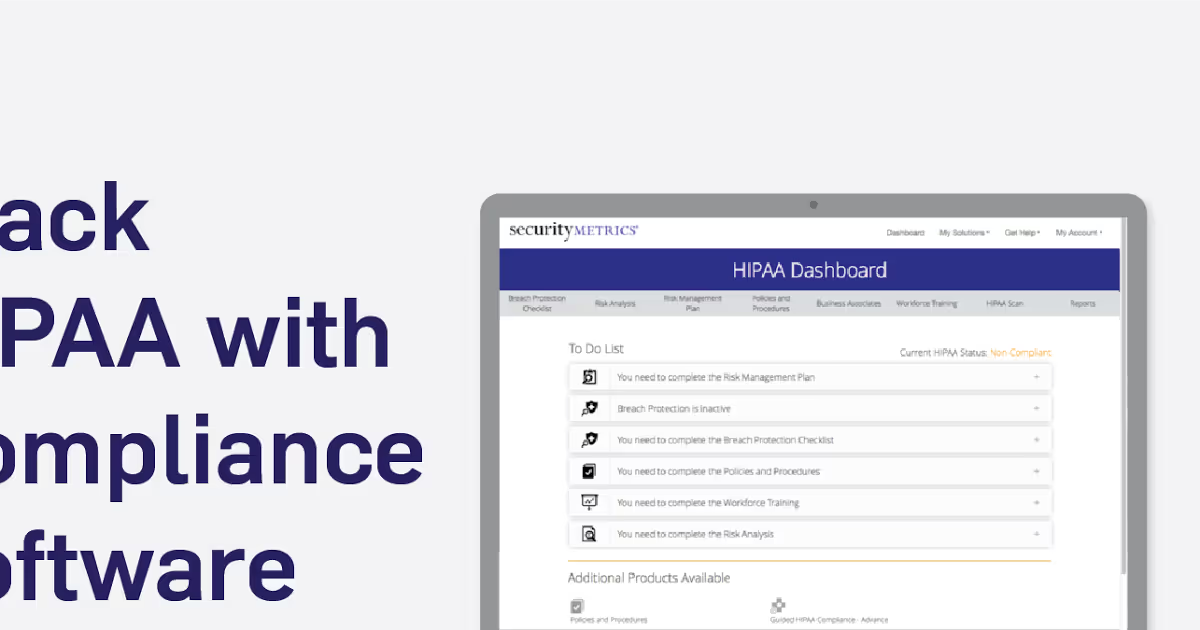
This HIPAA compliance software is easy to update and doubles as a documentation tool.
Don’t let human hackers disorient your employees.

Having the proper security budget protects not just your organization, but your patients as well.
Don’t be afraid of the cloud; just be smart with it.
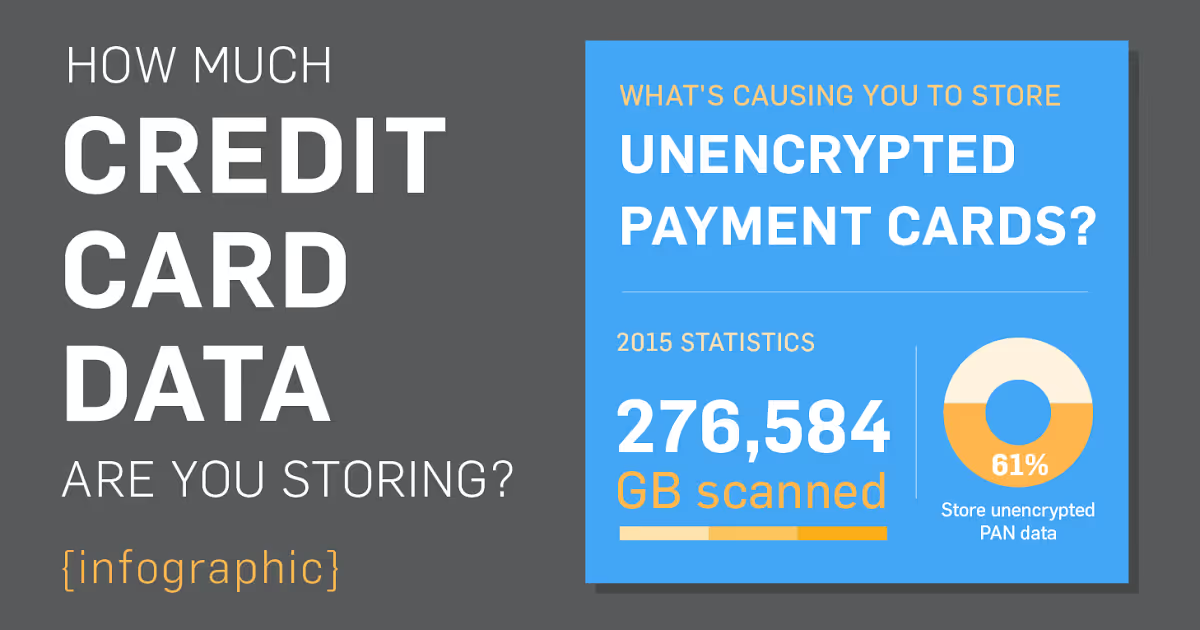
See the unencrypted storage results from SecurityMetrics’ latest PANscan reports.

Anti virus doesn’t protect; it cleans up malware infections after the fact.

Unfortunately, many healthcare organizations aren’t properly securing their medical devices, leaving them open to cyber attacks.
The New Samba vulnerability could expose companies to man-in-the-middle attacks.

SecurityMetrics HIPAA solution testimonials from real healthcare entities like you.
Learn how to find PCI scope, reduce it, and protect your cardholder data.

Don’t let employee cyber security training fall to the side.

See how healthcare organizations are managing their firewalls. Do you know if your firewalls are HIPAA compliant?

Holiday Security Tips: While the busyness of the holidays can provide cover for cybercriminal activity, there are a few things your business can do to protect against data breaches this holiday season.

Learn how to prepare for a data breach by conducting drills, exercises, and security trainings Massive data breaches—and their devastating aftermath—are increasing in frequency.

With the EU’s GDPR compliance date looming (May 25, 2018), businesses are in varying states of readiness and awareness. Many are likely wondering, should I be worried?

If you are a merchant, or any organization that handles the personal data of European Union citizens, you will need to comply with the GDPR. Here are three ways you can make progress today towards your GDPR compliance.

Properly identifying and addressing attack surfaces requires scoping, specialization, and the help of security professionals.
We caution all SecurityMetrics customers, merchants, and businesses to remain extra vigilant around cyber threat actors who are exploiting this global crisis to their advantage.

The SecurityMetrics Threat Intelligence Center has observed a disturbing trend in data breach responses over the past few months of businesses downplaying the severity of data breaches using a variety of tactics and techniques.

The global pandemic has created more opportunities for ransomware threat actors to create mayhem and chaos across the threat landscape.

Did you know that protected Health Information (PHI) is extremely valuable to hackers, even more so than credit card data?

This blog addresses cybersecurity workforce training FAQs and provides many resources to help businesses strengthen their security and train their employees.

The results from Shopping Cart Inspect have been insightful into the current and future attack methods in ecommerce. Here are our Ecommerce Security Trends From 2021.