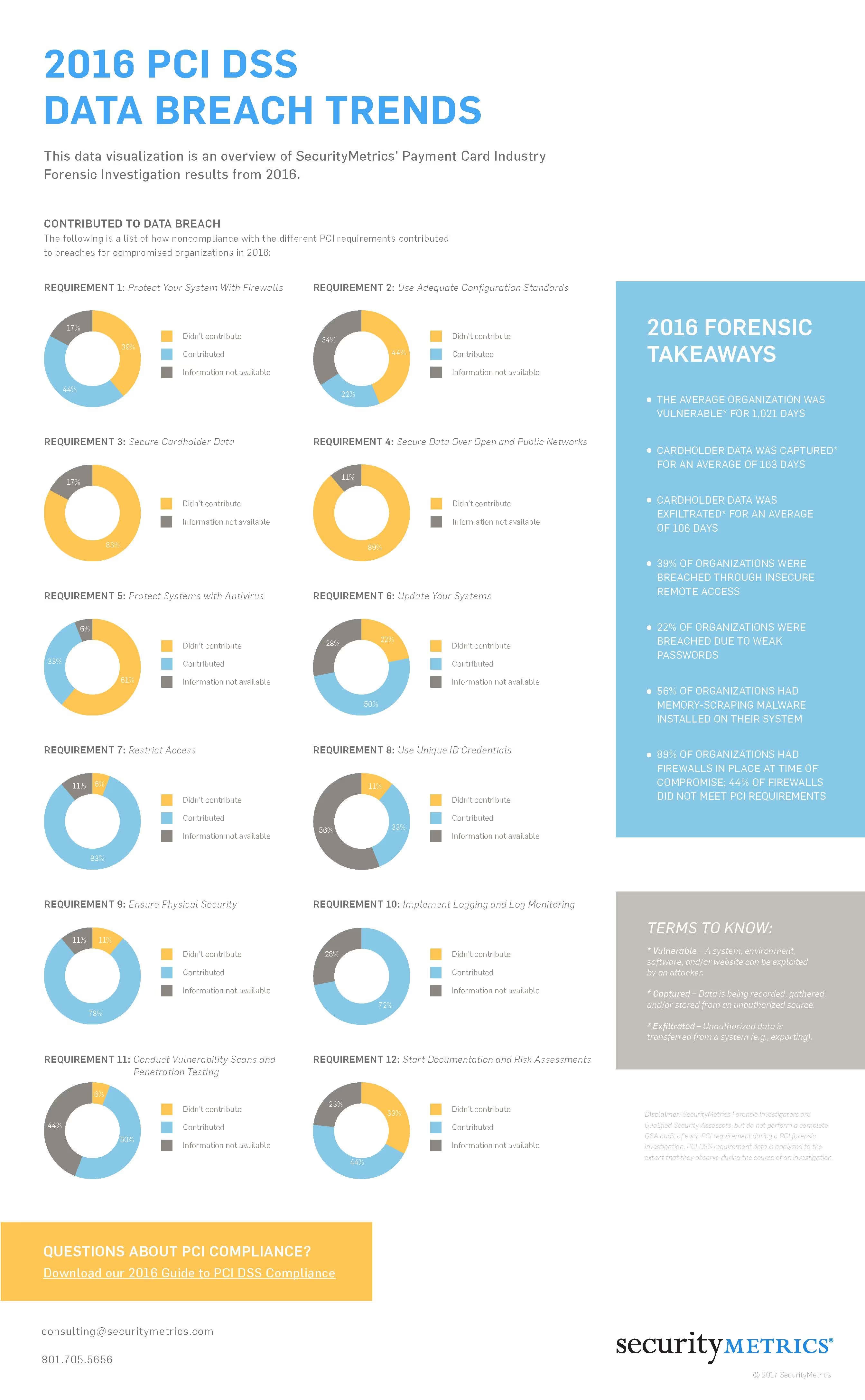
Data Breach Trends
Over the years, our forensic investigators have witnessed the rise and fall of popular cyber attack trends. Find out more about their findings here.
Over the years, our forensic investigators have witnessed the rise and fall of popular cyber attack trends. Find out more about their findings here.
SecurityMetrics Forensic Investigation Results from 2020
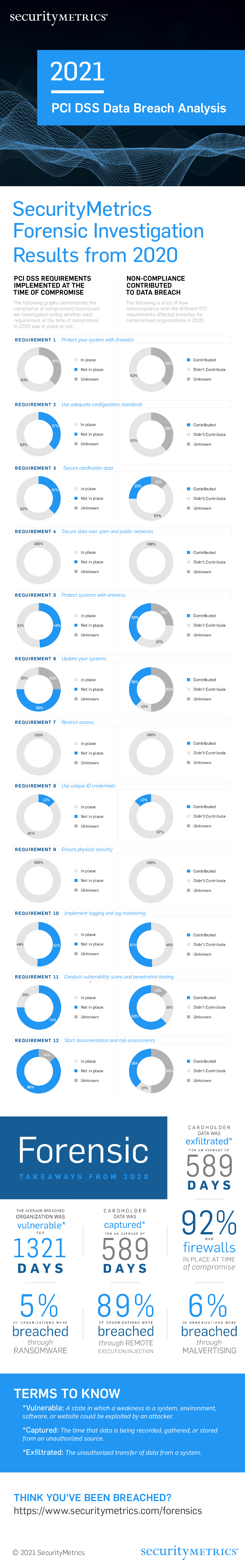
The following graphs demonstrate the compliance of compromised businesses we investigated noting whether each requirement at the time of compromise in 2020 was in place or not:
REQUIREMENT 1: Protect Your System With Firewalls
REQUIREMENT 2: Use Adequate Configuration Standards
REQUIREMENT 3: Secure Cardholder Data
REQUIREMENT 4: Secure Data Over Open and Public Networks
REQUIREMENT 5: Protect Systems with Antivirus
REQUIREMENT 6: Update Your Systems
REQUIREMENT 7: Restrict Access
REQUIREMENT 8: Use Unique ID Credentials
REQUIREMENT 9: Ensure Physical Security
REQUIREMENT 10: Implement Logging and Log Monitoring
REQUIREMENT 11: Conduct Vulnerability Scans and Penetration Testing
REQUIREMENT 12: Start Documentation and Risk Assessments
The following is a list of how noncompliance with the different PCI requirements affected breaches for compromised organizations in 2020:
REQUIREMENT 1: Protect Your System With Firewalls
REQUIREMENT 2: Use Adequate Configuration Standards
REQUIREMENT 3: Secure Cardholder Data
REQUIREMENT 4: Secure Data Over Open and Public Networks
REQUIREMENT 5: Protect Systems with Antivirus
REQUIREMENT 6: Update Your Systems
REQUIREMENT 7: Restrict Access
REQUIREMENT 8: Use Unique ID Credentials
REQUIREMENT 9: Ensure Physical Security
REQUIREMENT 10: Implement Logging and Log Monitoring
REQUIREMENT 11: Conduct Vulnerability Scans and Penetration Testing
REQUIREMENT 12: Start Documentation and Risk Assessments
SecurityMetrics Forensic Investigation Results from 2019
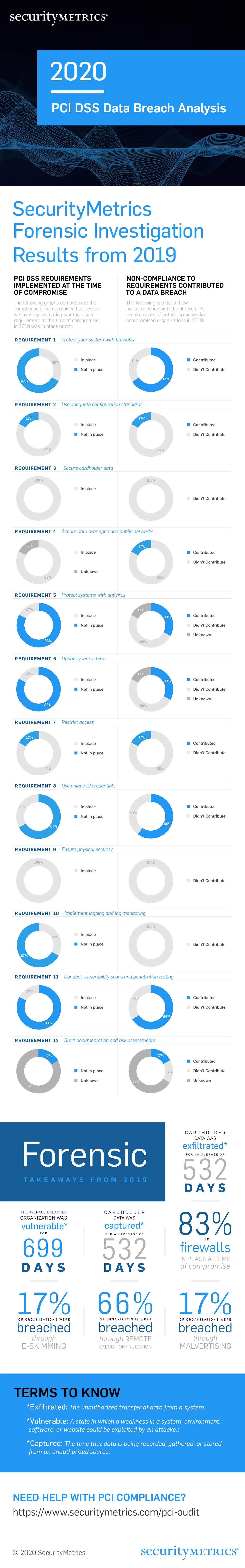
The following graphs demonstrate the compliance of compromised businesses we investigated noting whether each requirement at the time of compromise in 2019 was in place or not:
REQUIREMENT 1: Protect Your System With Firewalls
REQUIREMENT 2: Use Adequate Configuration Standards
REQUIREMENT 3: Secure Cardholder Data
REQUIREMENT 4: Secure Data Over Open and Public Networks
REQUIREMENT 5: Protect Systems with Antivirus
REQUIREMENT 6: Update Your Systems
REQUIREMENT 7: Restrict Access
REQUIREMENT 8: Use Unique ID Credentials
REQUIREMENT 9: Ensure Physical Security
REQUIREMENT 10: Implement Logging and Log Monitoring
REQUIREMENT 11: Conduct Vulnerability Scans and Penetration Testing
REQUIREMENT 12: Start Documentation and Risk Assessments
The following is a list of how noncompliance with the different PCI requirements affected breaches for compromised organizations in 2019:
REQUIREMENT 1: Protect Your System With Firewalls
REQUIREMENT 2: Use Adequate Configuration Standards
REQUIREMENT 3: Secure Cardholder Data
REQUIREMENT 4: Secure Data Over Open and Public Networks
REQUIREMENT 5: Protect Systems with Antivirus
REQUIREMENT 6: Update Your Systems
REQUIREMENT 7: Restrict Access
REQUIREMENT 8: Use Unique ID Credentials
REQUIREMENT 9: Ensure Physical Security
REQUIREMENT 10: Implement Logging and Log Monitoring
REQUIREMENT 11: Conduct Vulnerability Scans and Penetration Testing
REQUIREMENT 12: Start Documentation and Risk Assessments
https://info.securitymetrics.com/2019-data-breach-analysis
Results from 2018 SecurityMetrics Forensic Investigations
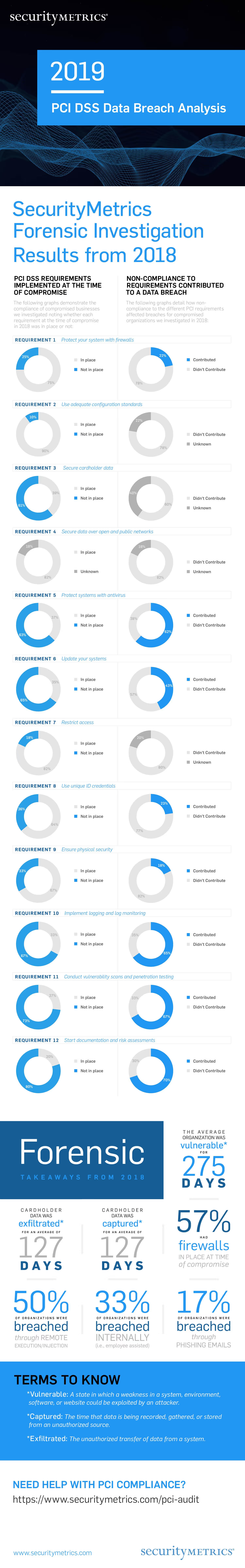
SecurityMetrics Forensic Investigators have witnessed the rise and fall of popular attack trends over 16 consecutive years.
Comparing 2018 forensic trends to previous years, SecurityMetrics’ Forensic Investigators conducted more forensic e-commerce investigations than point-of-sale (POS) environments. For example, in 2018, approximately 80% of payment-card-related investigations were of e-commerce breaches compared to 2017 where only 33% of investigations were e-commerce breaches.
The following data visualization is an analysis of SecurityMetrics’ Payment Card Industry Forensic Investigation results from 2018:
The following graphs demonstrate the compliance of compromised businesses we investigated noting whether each requirement at the time of compromise in 2018 was in place or not:
REQUIREMENT 1: Protect Your System With Firewalls
REQUIREMENT 2: Use Adequate Configuration Standards
REQUIREMENT 3: Secure Cardholder Data
REQUIREMENT 4: Secure Data Over Open and Public Networks
REQUIREMENT 5: Protect Systems with Antivirus
REQUIREMENT 6: Update Your Systems
REQUIREMENT 7: Restrict Access
REQUIREMENT 8: Use Unique ID Credentials
REQUIREMENT 9: Ensure Physical Security
REQUIREMENT 10: Implement Logging and Log Monitoring
REQUIREMENT 11: Conduct Vulnerability Scans and Penetration Testing
REQUIREMENT 12: Start Documentation and Risk Assessments
The following is a list of how noncompliance with the different PCI requirements affected breaches for compromised organizations in 2018:
REQUIREMENT 1: Protect Your System With Firewalls
REQUIREMENT 2: Use Adequate Configuration Standards
REQUIREMENT 3: Secure Cardholder Data
REQUIREMENT 4: Secure Data Over Open and Public Networks
REQUIREMENT 5: Protect Systems with Antivirus
REQUIREMENT 6: Update Your Systems
REQUIREMENT 7: Restrict Access
REQUIREMENT 8: Use Unique ID Credentials
REQUIREMENT 9: Ensure Physical Security
REQUIREMENT 10: Implement Logging and Log Monitoring
REQUIREMENT 11: Conduct Vulnerability Scans and Penetration Testing
REQUIREMENT 12: Start Documentation and Risk Assessments
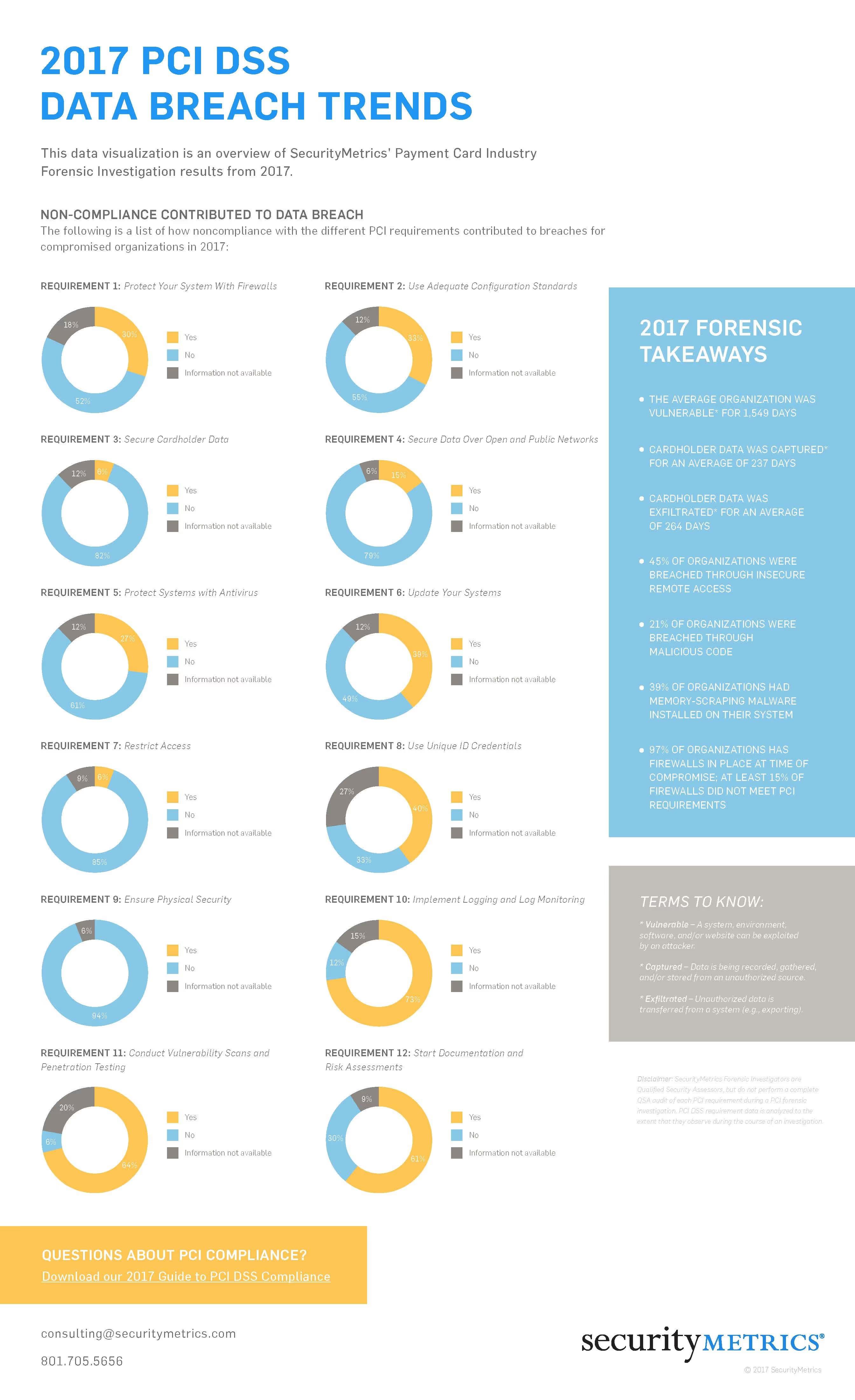
http://info.securitymetrics.com/infographic-data-breach-visualization-2017
Results from 2017 SecurityMetrics Forensic Investigations
http://info.securitymetrics.com/2016-data-breach-trends
Results from 2016 SecurityMetrics Forensic Investigations