5 Tips to Implement Security Awareness at Your Company
Whether you’re a CIO, the head of IT, or in a non-security-related position, if your data security practices are unclear, your company is at a greater risk to a data breach.

Whether you’re a CIO, the head of IT, or in a non-security-related position, if your data security practices are unclear, your company is at a greater risk to a data breach.

Unfortunately, there is no “silver bullet” solution to close the gaps in your data security and compliance. Both require time, education, planning, and buy-in. Preventing data breaches at companies is largely about creating clear internal messaging and successfully disseminating that messaging throughout your organization.
Whether you’re a CIO, the head of IT, or in a non-security-related position, if your data security practices are unclear, your company is at a greater risk to a data breach. Here are 5 tips that will help you implement more security awareness and security training at your company to protect sensitive information like payment card data, personally identifiable information (PII), or protected health information (PHI) at your organization:
Data security begins (and ends) with documentation. The more time and detail you put into your documentation, the better foundation your security culture will have. You will use your policies and procedures as evidence of compliance, for employee training, and to support day-to-day operations. Give your employees easy access to reliable and updated security information.
Your policies and procedures should include things like:
You should also include the data security compliance mandates you may be required to follow—like PCI DSS, HIPAA, and GDPR.
Also, be sure that once you create the policies and procedures, you don’t just set them on the shelf and forget about them. Make these documents a central part of the office. Feature your policies and procedures in your trainings and schedule time to update them regularly. Good data security is all about proper process. Documentation is key in that process.
Managing sensitive data from day to day involves many people, processes, and technologies. Some of the controls and areas you'll need to work with include:
Not surprisingly, managing your company’s sensitive data includes a significant documentation component, and should begin with a risk assessment. Risk assessments include data mapping, listing vulnerabilities and threats, analyzing risk, creating a risk management plan, and testing your environment.
Here is an example of data flow diagram created to map the flow of protected health information (PHI):
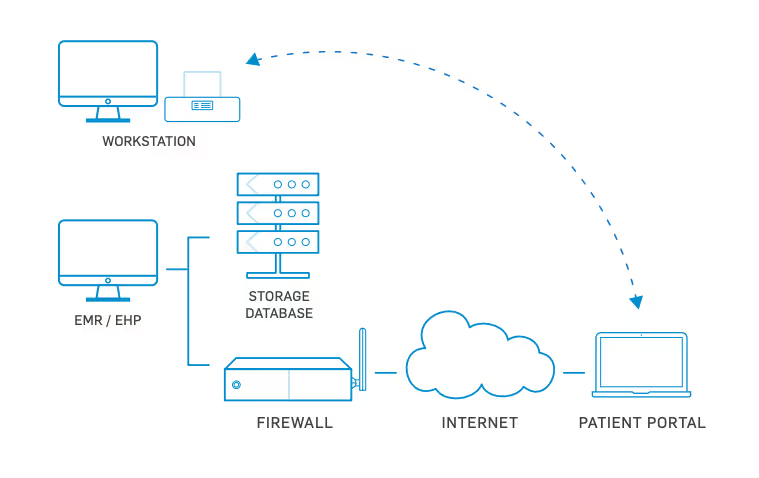
READ ALSO: Network Diagrams: Key to Compliance and Security
The correct security tools are critical to protecting data at your company. Data breaches are prevalent due to a lack of appropriate tools–plus, they aren’t always used or configured correctly. Yours will likely include some or all of the following:
It’s important to educate yourself and avoid buying products blindly, without understanding the different types of security tools, what they do, or if they are even necessary for your environment. Once you purchase tools, be sure to provide training and awareness to those who need it.
Data breach attacks are inevitable. If these attacks are successful and your data is compromised, you will be glad you already have a response plan in place. Depending on what security mandate(s) you comply with, you could face significant fines. We’ve seen data breach fines so severe they put companies out of business.
Different compliance mandates may require different breach procedures, especially regarding how you notify, who you notify, and when you decide to notify. To help implement security awareness, begin your data breach response and start getting the word out.
Include updates on your efforts in internal newsletters, emails, meetings, trainings, announcements, and dashboards.
The success of your data breach response plan hinges on communication. Have you noticed a theme in this post? If you have the plan on file, but no one knows about it, your employees will waste a lot of time scrambling to organize a response to the breach right after it happens.
A proper data breach response plan will include things like a pre-written PR response, a contact list for emergency communications, and a forensic analysis list to begin your in-house forensic process. Training should include topics like roles, possible scenarios, and a heavy emphasis on what not to do (for example, don’t automatically wipe all your data if a breach occurs). Trainings should also include testing your data breach response plan. Learn about the difference between testing with discussion-based exercises, tabletop exercises, and parallel testing here.
When it comes to compliance, it’s your responsibility to train, educate, and bring all employees on board. There are many different kinds of compliance that require data security controls. At SecurityMetrics, we primarily work with the PCI DSS, HIPAA, and GDPR.
Each of these data security mandates carries its own unique requirements and non-compliance fees. There is some crossover in terms of requirements and security controls, but each mandate was created for a separate reason and to protect different types of data.
PCI DSS stands for the Payment Card Industry Data Security Standard, and is a written mandate created for companies that take and process payment transactions using major card brands like Visa, MasterCard, and American Express. These card brands created the PCI DSS in an effort to help regulate the industry, and most importantly, to help businesses and customers avoid card data theft and fraud.
If your company processes, stores, or transmits payment card data, you are likely required to become PCI compliant.
Check out: How much Does PCI Compliance Cost?
HIPAA stands for Health Insurance Portability and Accountability Act. HIPAA was enacted in the US in 1996. Title II of HIPAA includes the Privacy, Security, and Breach Notification rules, which are intended to help protect medical information. A main purpose of the HIPAA privacy and security rules is to protect electronic protected health information (ePHI) from being compromised, which usually occurs as a result of a hacker, unauthorized access, or employee negligence.
If you are a healthcare-related covered entity or business associate and you process or retain protected health information (PHI), you likely need to comply with HIPAA.
GDPR is a newly enacted data privacy mandate (as of May 25, 2018), passed in the EU and intended to protect the sensitive and private data of EU citizens. If you handle the data of EU citizens–even if your business is located outside of the EU–you are required to follow the requirements of GDPR.
Learn about GDPR here: GDPR 101 Part 1, GDPR 101 Part 2, GDPR 101 Part 3
Data breaches can cause small businesses to fold and large businesses to suffer huge losses in capital and reputation. Security awareness at a company will not take hold without significant support from the top. As we mentioned above, preventing data breaches takes time, resources, and planning. Depending on the size of your company and the data mandate you follow, you may delegate security awareness to a CISO, an IT team lead, or you might need to lead the charge.
No matter your situation, you need a trusted and easy-to-use source for education.
We created Academy to help people better understand the layers needed for data security. Academy is free, and comes from over 19 years of industry knowledge.
Academy gives an overview of what data security is, and what’s needed to achieve it. It educates users on how security fits into compliance and vice versa. Now, proactive business owners and IT teams to have a free resource that encourages informed security buying and management.
We secure peace of mind for organizations that handle sensitive data. We hold our tools, training, and support to a higher, more thorough standard of performance and service. Never have a false sense of security.™
We are a PCI certified Approved Scanning Vendor (ASV), Qualified Security Assessor (QSA), Certified Forensic Investigator (PFI), and Managed Security provider with over 20 years of data security experience. From local shops to some of the world’s largest brands, we help all businesses achieve data security through managed services and compliance mandates (PCI, HIPAA, GDPR, HITRUST). We have tested over 1 million systems for data security and compliance. We are privately held and are headquartered in Orem, Utah, where we maintain a Security Operations Center (SOC) and 24/7 multilingual technical support.