
The PCI DSS 3.2 has recently made some changes to multi-factor authentication.

If your business collects, transmits, or stores cardholder and credit card data, you need to be PCI compliant. Here are 7 PCI compliance tips for small businesses.
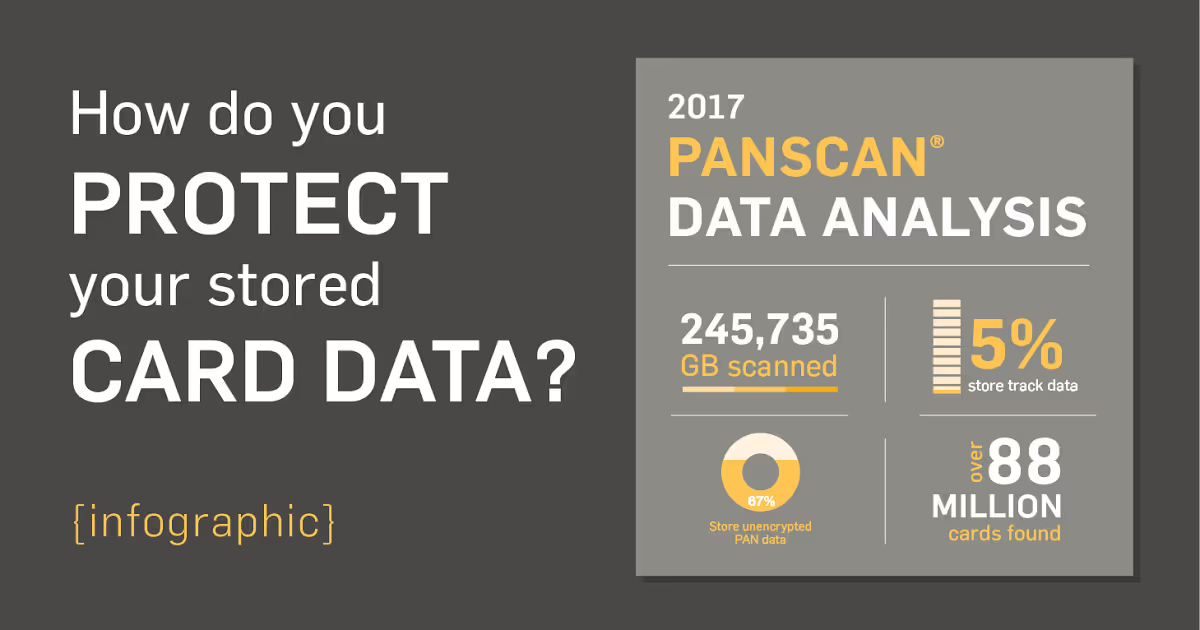
More businesses store unencrypted card numbers than you think, and the numbers have gone up this year.

The PCI SSC released a guidance for e-commerce websites.

2017 was a year marked by massive hacks like Equifax, rampant malware like WannaCry and Petya, notable vulnerabilities like KRACK, as well as changes to and guidance about the Payment Card Industry Data Security Standard (PCI DSS).

How did organizations do with HIPAA compliance in 2017? Here are the results along with major takeaways to help you with your own HIPAA compliance efforts.

See how much unencrypted card data PANscan® found on business networks in 2017.

A reference for business associates using the SecurityMetrics HIPAA Guide at their organizations.

We’ve rounded up some of the most helpful topics from our blog to help set you on the right course for 2019. Prepare now, so you’ll have less hassle later.

10 misconceptions about security audits and questions you should ask when getting audited. The focus of this blog will be how to have better data security and compliance technology so that you can avoid data breaches, costly fines, slow downs, and hindrances to your business.

Choose your vendors wisely and make sure you have a Business Associate Agreement (BAA) in place.

Here are 5 trends in payments that every business should watch out for this year.

If you truly lived by everything PCI DSS requires, implementing a P2PE solution would very possibly cost you less money, no matter your size.

It’s simple to protect patient data from malware with the right tools, controls, and people in place.

Depending on the size and environment of your company, security consistency can be a real challenge.

Take a look at three methods you can use them to get merchants excited about PCI DSS.

Here are 5 tips for enterprise organizations to get PCI compliant more efficiently.

5 Security Best Practices for Protecting Your HIPAA-Compliant Data: encrypt everything, assess your risk, train your people, be vigilant and ready to act, and read buisness associate agreements and find partnerships you trust.

What is network penetration testing? PCI DSS Requirement 11 calls for regular vulnerability scanning and penetration testing.

The FBI has reported an increase in discovered and reported attacks against all organizations, with 83% of ransomware attacks against healthcare.

PCI DSS compliance is not only a great tool for protecting payment data, but overall data security.

2022 Forensic Predictions: SecurityMetrics Forensic Investigators have witnessed the rise and fall of popular attack trends over 20 consecutive years.